Note: Updated 2019/June with information regarding MDS as well as change of recent CFL-R microcode vulnerability reporting.
We are pleased to release SP4/a/c (version 28.69) update for Sandra Titanium (2018) with the following updates:
Sandra Titanium (2018) Press Release
- Reporting of Operating System (Windows) speculation control settings for the recently discovered vulnerabilities:
- Kernel Retpoline mitigation status (for RDCL) in recent Windows 10 / Server 2019 updates
- Kernel Address Table Import Optimisation (“KATI”) status (as above)
- L1TF – L1 data terminal fault mitigation status
- MDS – Microarchitectural Data Sampling/”ZombieLoad” mitigation status
- Hardware Support:
- AMD Ryzen2 (Matisse), Stoney Ridge support
- Intel CometLake (CML), CannonLake (CNL), IceLake (ICL) support (based on public information)
- CPU Benchmarks:
- Image Processing: SIMD code improvement (SSE2/SSE4/AVX/AVX2-FMA/AVX512)
- Multi-Media: Lock-up on NUMA systems (e.g. AMD ThreadRipper) thanks to Rob @ TechGage.
- Memory/Cache Benchmarks
- Return memory controller firmware version to Ranker
- GPGPU Benchmarks:
- CUDA SDK 10.1
- OpenCL: Processing (Fractals/Mandelbrot) variable vector width based on reported FP16/32/64 optimal SIMD width.
- Ranker, Price & Information Engines
- HTTPS (encryption) support for all engines as well as the main website
What is Retpoline?
It is a mitigation against ‘Spectre‘ 2 variant (BTI – Branch Target Injection) that affects just about all CPUs (not just Intel but AMD, ARM, etc.). While ‘Spectre’ does not have the same overall performance impact degradation as ‘Meltdown‘ (RDCL – Rogue Data Cache Load) it can have a sizeable impact on some processors and workloads. At this time no CPUs contain hardware mitigation for Spectre without performance impact.
Retpoline (Return Trampoline) is a faster way to mitigate against it without restricting branch speculation in kernel mode (using IBRS/IBPB) and has recently been added to Linux and now Windows version 1809 builds with KB4482887. Note that it still needs to be enabled in registry via the Mitigation Features Override flags as by default it is not enabled.
What CPUs can Retpoline be used on?
Unfortunately Retpoline is only safe to use on some CPUs: AMD CPUs (though does not engage on Ryzen, see below), Intel Broadwell or older (v5 and earlier) – thus not Skylake (v6 or later).
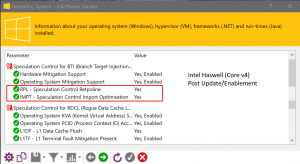
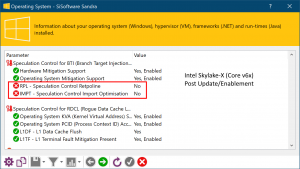
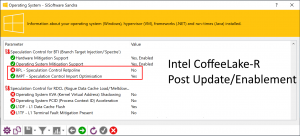
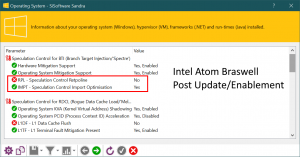
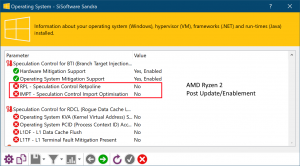
Windows speculation control settings reporting:
From our somewhat limited testing above it seems that:
- Intel Haswell/Broadwell (Core v4/v5) and perhaps earlier (Ivy Bridge/Sandy Bridge Core v3/v2) users are in luck, Retpoline is enabled and should improve performance; unfortunately RDCL (“Meltdown” mitigation) remains.
- Intel Coffeelake-R (Core v8r refresh), Whiskylake ULV (v8r)
users do benefit a bit more for their investment – while Retpoline is not enabled, KATI is enabled and should help. Not requiring KVA is the biggest gain of CFL-R.2019/June: latest microcode (AEh) causes Windows to require KVA/L1TF thus negating any benefit CFL-R had over original CFL/KBL/SKL.
- Intel Skylake (Core v6), Kabylake (v7) and Coffeelake (v8) are not able to benefit from Retpoline but KATI can work on some systems (driver dependent). However, on our Skylake ULV, Skylake-X test systems KATI could not be enabled. We are investigating further.
- Intel Atom (v4/v5+) users should be able to use Retpoline but it seems it cannot be enabled currently. KATI is enabled.
- AMD Ryzen (Threadripper) 1/2 users should also be able to use Retpoline but it seems it cannot be enabled currently. While RDCL is not required, mitigations for Spectre v2 are required and should be enabled. We are investigating further.
Reviews using Sandra 2018 SP4:
- AMD Ryzen 2 Mobile (2500U) CPU Performance
- AMD Ryzen 2 Mobile (2500U) Cache & Memory Performance
- AMD Ryzen 2 Mobile (2500U) Vega 8 GP(GPU) Performance
Update & Download
Commercial version customers can download the free updates from their software distributor; Lite users please download from your favourite download site.